CONTENTS
A
network is composed of a large number of entities that work together in order to
provide some services to the end user. Computer networks have revolutionized our
use of computers. They pervade our everyday life. We are in an information age
and computer networks are becoming an integral part in the dissemination of
information.
In the course of doing research,
it has been found that it has taken on several distinct meanings. One is that
Ping is actually an acronym for the words 'Packet INternet Groper'.
Another is that it is in fact not an acronym at all, but a noun that was adopted
from a verb that the US Navy that uses to describe what its submarines do when
looking for objects under the sea. Their subs send out sonar waves and then wait
for a return wave when it bounces off something, such as another sub, whale,
ocean floor etc. This, in turn, was adopted from bats and dolphins, which
navigate in roughly the same way. This is what a system administrator does when
Ping is used. As such, Ping has also evolved into a verb in the computer
industry, and it is used in somewhat the same manner of the Navy.
The Ping utility is essentially a
system administrator's tool that is used to see if a computer is operating and
also to see if network connections are intact. Ping uses the Internet Control
Message Protocol (ICMP) Echo function, which is detailed in RFC 792. A small
packet is sent through the network to a particular IP address. This packet
contains 64 bytes - 56 data bytes and 8 bytes of protocol reader information.
The computer that sent the packet then waits (or 'listens') for a return packet.
If the connections are good and the target computer is up, a good return packet
will be received. PING can also tell the user the number of hops that lie
between two computers and the amount of time it takes for a packet to make the
complete trip. Additionally, an administrator can use Ping to test out name
resolution. If the packet bounces back when sent to the IP address but not when
sent to the name, then the system is having a problem matching the name to the
IP address. As mentioned previously, Ping has also evolved from a noun/acronym
into a verb, for example: "Ping server X to see if it is up" The time
it takes for the packet to get to the target computer and back again is known as
the round trip time. If this takes an extended period of time, it is indicative
that something may be wrong.
The goal of this project is to find out whether the destination host, we are trying to PING, is alive or not. i.e. whether the destination host is connected to the network or not.
What
Ping can tell you
Ping places a unique sequence number on each packet it transmits, and reports, which sequence numbers it receives back. Thus, you can determine if packets have been dropped, duplicated, or reordered.
Ping checksums each packet it exchanges. You can detect some forms
of damaged packets.
Ping places a timestamp in each packet, which is echoed back and
can easily be used to compute how long each packet exchange took - the Round
Trip Time (RTT).
What
Ping can not tell you
Some routers may silently discard undeliverable packets. Others may
believe a packet has been transmitted successfully when it has not been. (This
is especially common over Ethernet, which does not provide link-layer
acknowledgments) Therefore, Ping may not always provide reasons why packets go
unanswered.
Ping cannot tell you why a packet was damaged, delayed, or duplicated. It
cannot tell you where this happened either, although you may be able to deduce
it.
Ping cannot give you a blow-by-blow description of every host that handled the packet and everything that happened at every step of the way. It is an unfortunate fact that no software can reliably provide this information for a TCP/IP network.
TCP/IP
is a set of protocols developed to allow co-operating computers to share
resources across a network. A community of researchers centred on the ARPANET
developed these set of protocols.
TCP/IP
is a family of protocols. A few provide ‘low-level’ functions
needed for many applications. These include IP (Internet Protocol), TCP
(Transmission Control Protocol) and UDP (User Datagram Protocol).
Other protocols are for specific tasks like transferring files between
computers (FTP), sending mail (SMTP, POP3), or finding
out who is logged in on another computer.
Since
TCP and IP are two of the important protocols of the ‘Internet
Protocol’ suite, it is sometimes referred to as ‘TCP/IP Protocol
Suite’.
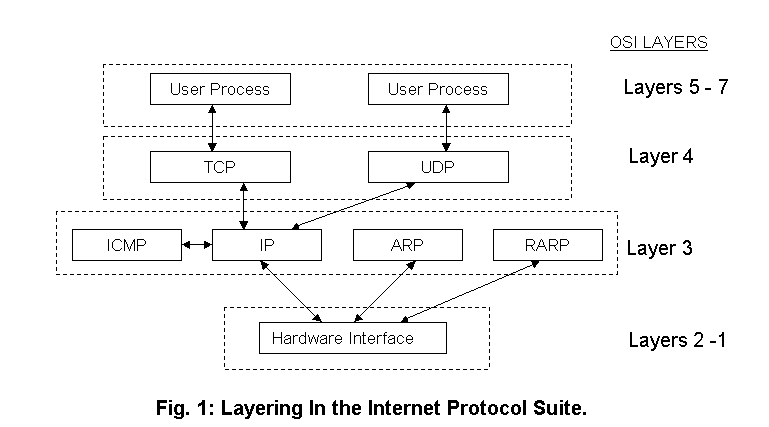
The
working of our program is implemented in layer 3 of the ISO’s OSI Model.
This layer is the Network Layer.

The
layering in the Internet protocol suite consisting of the network layer along
with its inner parameters is as shown in the Fig. [1].
Transmission
Control Protocol
(TCP): This is a connection-oriented protocol that provides a reliable, full
duplex, byte stream for a user process. Most Internet applications use TCP.
User
Datagram Protocol
(UDP): This provides an unreliable connectionless delivery service using IP to
transport messages between machines. It uses IP to carry messages, but adds the
ability to distinguish among multiple destinations within a given host computer.
Also, since the routing is done dynamically, it is robust.
Internet
Control Message Protocol
(ICMP): This is the protocol to handle error and control information between
gateways and hosts; while ICMP messages are transmitted using IP datagrams,
these messages are normally generated and processed by the TCP/IP networking
software itself and not by user/application processes. ICMP
also includes an echo request/reply used to test whether a destination is
reachable and responding.
Internet
Protocol
(IP): This protocol provides the basis for connectionless, best–effort packet
delivery service. IP includes the ICMP control and error message protocol as an
integral part. The protocol suite is often referred to as TCP/IP because TCP and
IP are the two fundamental protocols.
Address
Resolution Protocol
(ARP): The TCP /IP protocols use ARP to dynamically bind high-level IP address
to a low-level physical address. ARP is used across a single physical network
and is limited to networks that support hardware broadcast.
Reverse
Address Resolution Protocol
(RARP): This protocol uses physical network addressing to obtain the machine’s
Internet address.
Linux
is a 32-bit operating system that uses the minimal resources, without
sacrificing functionality. The Linux software is developed under ‘Open and
Free Distribution’ conditions. This means that anyone can become involved
if they are able to and allows anyone to find out how the system works and to
trace and remove any bugs. With their built-in support, Linux computers can be
linked into existing networks without any problem.
The main characteristics are:
Multitasking:
all processors run entirely independently of each other.
Multi-user:
Linux allows a number of users to work with the system at the same time.
Multi-processing:
The operating system can distribute several applications across several
processors.
Architecture
independence:
Linux runs on several hardware platforms.
A
fundamental entity in a computer network is a process. A process
is a program that is being executed by the computer’s operating system. If two
computers are communication with each other, it means two processes, one running
on each computer, are in communication with each other. For two processes to
communicate with each other, they must both agree to it.
Unix/Linux
provides various forms of IPC like pipes, FIFOs, message queues,
semaphores and shared memory. Network programming involves the
interaction of two or more processes on different systems. Sockets (BSD)
and Transport Layer Interface or TLI (System V) are forms of IPC provided
for both, communication between processes on a single system and between
processes on different system.
The
standard model for network applications is the client-server model. A server
is a process that is waiting to be contacted by a client process, so that
the server can do something that the client has requested for.
A
signal is a notification to a process that an event has occurred. Signals
usually occur asynchronously, that is, the process doesn’t know ahead of time
exactly when a signal will occur. Signals can be sent,
By one
process to another process or to itself
By the kernel
to a process
Signals
are generated,
If kill
system call is used,
If kill
command is used which issues a kill system call,
By terminal
characters like ctrl-c, delete or ctrl-backslash,
By certain
hardware conditions and,
By certain
software conditions.
Whenever
a specific type of signal occurs, a process can provide a function called ‘signal
handler’, which is invoked to do whatever the process wants to do to
handle the condition. This is called catching the signal. A process can
choose to ignore a signal or allow the default action to happen. Normally, a
process is terminated on receipt of a signal.
Socket
is one of the methods of inter-process communication that allows developing true
distributed client/server applications to run across networks. A socket
allows client/server systems to be developed either locally, on a single server,
or across networks. Socket mechanism can implement multiple clients
attached to a single server.
A
socket is one end point of two-way communication link between two
programs running on the network. Socket provides an endpoint for
communication for the Linux/Unix file access mechanism.
Sockets
can be connection oriented or connectionless, depending on whether
connection is opened with the other process prior to the communication or not.
Application programs request the operating system to create a socket when
one is needed, since socket provides an end point for communication.
The system call for socket requires three parameters to be mentioned, viz. the protocol family (specifies if the socket is used in Unix or Internet domain), the socket type (specifies the type of communication desired which include reliable stream service (SOCK_STREAM) and a connectionless datagram service (SOCK_DGRAM) and a ‘raw’ type (SOCK_RAW) that allows privileged programs to access low-level protocols or network interfaces), and lastly, the protocol to be used for communication through the socket (used to select a specific protocol namely ICMP, TCP, UDP or ‘raw’ type).
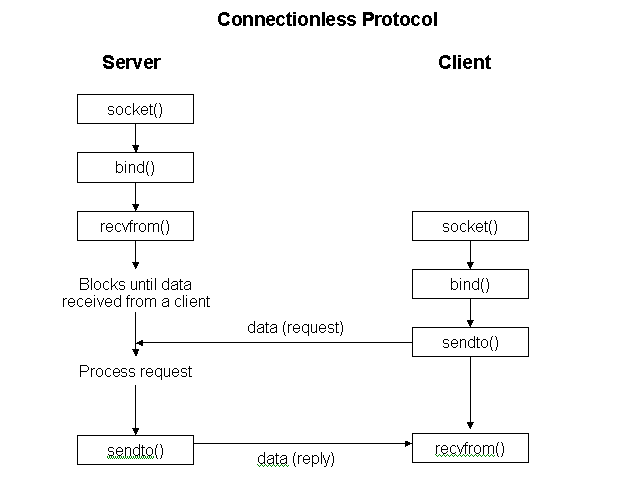
The ping client, that is being implemented, uses connectionless socket.
4.5.2
Socket Addresses:
Many
of the BSD networking system calls require a pointer to a socket address
structure as an argument. The definition of this structure is in <sys/socket.h>
For
the Internet family, the following structures are defined in <netinet/in.h>:
4.6.3 Byte ordering Routines:
Functions
that convert between the local machine byte order and the network standard byte
order are ntohs(), ntohl(), htons() and htonl().
4.6.4
Address
Conversion Routines:
Translation
between 32-bit IP address and the corresponding dotted decimal notation are
achieved by inet_addr(), which converts address in dotted form to 32-bit
address and inet_ntoa(), which does the reverse.
The
options can be set so as to affect a socket using the system call setsockopt().
The other functions are fcntl() and ioctl().
sockfd
argument must refer to an open socket descriptor, level specifies who in
the system is to interpret the option, the optval is a pointer to a user
variable from which an option is set, optlen is a value-result parameter
that is set to the size of optval before the call, and is then set by the
system on return to specify the amount of data stored into the optval
variable.
Unix/Linux
offers a set of library routines that performs useful functions related to
networking. Library routines are similar to procedures that a programmer binds
into a program. Library routines allow a process to obtain information from an
entry given any piece.
The
functions defined below are available for only Internet services. All these
functions return a pointer to the hostent structure defined as below:
The
‘gethostbyname’ and ‘gethostbyaddr’ are the library functions that allow
a process to retrieve information about a host given either its domain name or
its IP address respectively.
The
structure pointed to by the timeout argument is defined in <sys/time.h>
as:
The
request to select could be to check if readfds is ready for reading, or
if writefds is ready for writing or exceptfds has an exceptional
condition like arrival of out-of-band data for a socket pending. The kernel can
be instructed using this call to either return immediately after checking the
descriptors (timer value specified by the structure must be zero) OR return when
one of the file descriptors is ready for I/O, within the fixed time, which is
pointed to by the timeval structure OR return only when the specified
descriptors is ready for I/O i.e. wait indefinitely. The timeout argument
must be NULL. The descriptor values for each of the three arguments, readfds,
writefds and exceptfds are specified through the fd_set structure and
FD_xxx macros.
These
days, socket interface has become more popular and is being widely supported.
The word PING stands for ‘Packet Inter Net Groper’ and is used to describe the transmission of a sound wave to detect an underground object. Here, the Internet ping program is used to test the reach ability of another host on the Internet. We ping the other host by sending it ‘echo requests’ that it must respond to, if it is operational.
This
program sends an ICMP (Internet Control Message Protocol) echo request
message to a specified host and waits for a reply. A feature of using ICMP for
sending an echo request is that the operation of ICMP does not depend of
higher-level protocols, the TCP and UDP. Most of the TCP/IP implementations have
the facility of Ping program. This has proved to be a useful tool in discovering
network. This ping is also known as ‘Testing destination
reachability and
status’.
Our
program mainly deals with creating an ICMP packet. It is important to keep in
mind that even though ICMP messages are encapsulated and sent using IP, ICMP is
not considered a higher-level protocol, it is a required part of IP. The very
important reason for using IP to deliver ICMP message is that they need to
travel across several physical networks to reach their final destination. Thus,
ICMP cannot be delivered by physical transport alone.
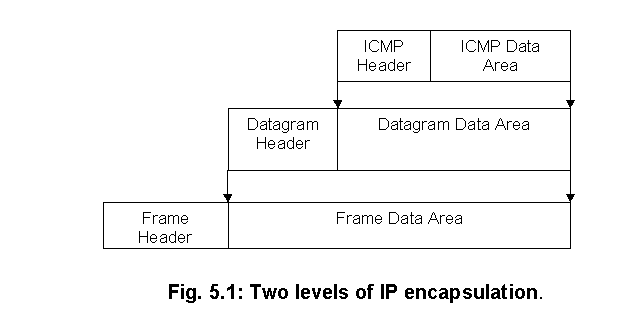
The
ICMP message is encapsulated in an IP datagram, which is further encapsulated in
a frame of transmission.
5.1.1
Format
of ICMP message
Every
ICMP message has its own format, but they all begin with:
An 8-bit
integer message TYPE field that identifies the message.
An 8-bit CODE
field that provides further information about the message type.
A 16-bit checksum
field. ICMP uses the same additive checksum algorithm as IP, but here the
ICMP checksum only covers the ICMP message.
In
addition to this, ICMP messages that report errors always include the header and
the first 64 bits of the datagram, which has caused the problem. The reason for
returning more than the datagram header alone is to allow the receiver to
determine more precisely which protocols and which application programs were
responsible for this. Higher-level protocols in the TCP/IP suite are designed so
that the critical information is encoded in the first 64 bits.
Some
of the ICMP ‘type’ field messages, which we use in our program, are defined
as below:
|
TYPE |
ICMP
MESSAGE TYPE |
|
0 |
Echo
reply |
|
3 |
Destination
Unreachable |
|
8 |
Echo
request |
|
11 |
Time
exceeded for datagram |
5.1.2 Echo request (type 8) and reply (type 0) message:

Here
a host or router sends an ICMP echo request message to a specified destination.
Any machine that receives an echo request formulates an echo reply
and returns it to the original sender. The request, which can contain optional
data in the data area, which is a variable length field, is returned as
it is, in the data section of the reply. The
fields Identifier and Sequence number are used by the sender to
match replies to requests.
The echo request and the associated reply can be used to
test whether a destination is reachable and responding. As both the request and
reply travel in IP datagrams, successful receipt of a reply/ack. verifies that
major pieces of the transport system are working fine.
5.1.3
ICMP
Destination Unreachable Message:
When
a router cannot forward or deliver the IP datagram, it sends a destination
unreachable message back to the original source, using the format shown below.

The Code field contains an integer that further describes the problem. Network (0), host (1), protocol (2) and port (3) unreachable are few of the important ones. Network unreachable errors usually imply routing failures; host unreachable errors imply delivery failures. Destinations may be unreachable because hardware is temporarily out of service or because the sender specified a nonexistent destination address. Protocol and port unreachable messages are generated when an invalid protocol or an invalid port number (a port is an abstract destination point used by higher level protocols like TCP and UDP to run services), where no host is running any process, is mentioned by the user in the outgoing datagram.
5.2.2 The UDP structure:
struct udphdr {5.2.3
The ICMP structure: (for echo request & reply only)
SYNOPSIS
ping
[ -drv ] host [ datasize ] [ npackets ]
DESCRIPTION
PING
uses the ICMP protocol's mandatory ECHO_REQUEST datagram to elicit an ICMP
ECHO_RESPONSE from a host or gateway. ECHO_REQUEST datagrams (“pings”) have
an IP and ICMP header, followed by a struct timeval and then an arbitrary number
of “pad” bytes used to fill out
the packet.
OPTIONS
-d
Set
the SO_DEBUG option on the socket being used. Essentially, this socket option is
not used by Linux kernel.
-r
Bypass
the normal routing tables and send directly to a host on an attached interface.
If the host is not on a directly-attached network, an error is returned.
-v
Verbose
output.
datasize
Specifies
the number of data bytes to be sent. The default is 56, which translates into 64
ICMP data bytes when combined with the 8 bytes of ICMP header data.
npackets
Stop after
sending count ECHO_REQUEST packets. With deadline option, ping
waits for count ECHO_REPLY packets, until the timeout expires.
When
using ping for fault isolation, it should first be run on the local host,
to verify that the local network interface is up and running. Then, hosts and
gateways further and further away should be ``pinged''. Round-trip times and
packet loss statistics are computed. If duplicate packets are received, they are
not included in the packet loss calculation, although the round trip time of
these packets is used in calculating the minimum/average/maximum round-trip time
numbers. When the specified number of packets has been sent (and received) or if
the program is terminated with a SIGINT, a brief summary is displayed. Shorter
current statistics can be obtained without termination of process with signal
SIGQUIT.
This program is intended for use in network testing, measurement and management. Because of the load it can impose on the network, it is unwise to use ping during normal operations or from automated scripts.
This
ping session shows a ten packet exchange over the loopback interface. One line
is printed for every reply received. Note that for each sequence number, a
single reply is received, and they are all in order. The IP TTL values are
reported, as are the round-trip times. Both are very consistent. At the end of
the session, statistics are reported. Pinging the loopback interface is a good
way to test a machine's basic network configuration, since no packets are
physically transmitted. Any problems in such a test are a cause for
alarm.
Stevens, W. Richard, “UNIX Network Programming”, 2001, 1st
Edition, Prentice Hall-India.
Tanenbaum, Andrew S., “Computer Networks”, 2001, 3rd
Edition, Prentice Hall-India.
RFC 792 - Internet Control Message Protocol, DARPA Internet Program
Protocol Specification
Connected: An Internet Encyclopedia
(http://www.freesoft.org/CIE/index.htm
The Ping Page (http://www.ping127001.com/index.htm)
Mike Muuss – The Story of PING
Manpages for PING